Why Securitization Should Be on a Distributed Ledger
Since digital asset prices began to falter in early 2018, the hype surrounding blockchain technology has moderated significantly. Although the speculators have largely moved on, believers in distributed ledger technology continue to tackle the challenges and complexities of blockchain development. While countless use cases are being explored, the financial services industry continues to put forward innovative solutions that aim to digitize traditional finance.
By Nelson Chu
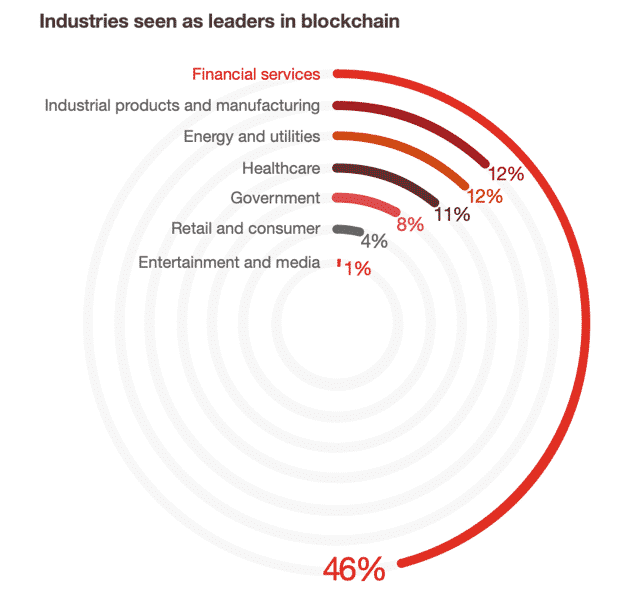
According to the 2018 Global Blockchain Survey conducted by PwC, the financial services industry emerges as the clear frontrunner amongst those industries exploring blockchain applications. From cross-border payment platforms to crypto-backed loans, there is no shortage of promising work in the financial services ecosystem. However, the digitization of conventional investment products remains a mostly untapped subset of the space.
Why Do Securitization and Digitization Work Together?
While securitization isn’t a new concept, some may not be aware of its functional purpose. In the world of conventional finance, securitization is the process of creating asset-backed securities. The process begins with pooling typically illiquid creditor assets such as leases, mortgages, loans, and credit card debt. These assets are then transformed into liquid securities that are sold to investors.
This process benefits both creditors and investors. Creditors free up cash from assets sitting on their balance sheet, and investors earn more competitive returns on their investment when compared to low-yielding public debt. Because the process of securitization emulates the concept of fractional ownership, it lends itself well to the digitization process. The “paper” securities created by conventional securitization could be adequately represented through digitization.
There is strong evidence that the future of asset securitization will run on distributed ledger technology. The prospect of streamlined operations, decreased costs, improved transparency, and strengthened security is appealing. Every party involved in the securitization process will reap the benefits of this technology. Also, the industry as a whole will be better equipped to handle both traditional and non-traditional assets.
The Type of Distributed Ledgers Suitable for Securitization
While it’s apparent that blockchain technology has the potential to transform the securitization process, selecting the appropriate network structure is crucial. Not every blockchain operates the same way, and securitization requires specific conditions to work effectively. Let’s first analyze the appropriateness of standard blockchain protocols as we explore securitization.
Public Distributed Ledgers
Public ledgers, as the name implies, allow anyone to write to the blockchain. This type of distributed ledger network is what most people conventionally understand as blockchain technology. For instance, both Bitcoin and Ethereum run on a public ledger in a fully decentralized manner.
Bitcoin is arguably the most well-known blockchain network as a result of its highly successful cryptocurrency. Ethereum has also garnered considerable press as a source of prolific decentralized application (DApp) development. Both of these platforms have helped to take blockchain mainstream, starting with Bitcoin in 2008 and Ethereum in 2015.
Private Distributed Ledgers
In contrast to public ledgers, a private or permissioned ledger is restricted to only approved participants. While private ledgers are still decentralized, network access is controlled, and transactions occur privately. A permissioned ledger requires some form of a central authority that assumes responsibility for vetting participants and determining the criteria necessary for writing to the ledger.
While a consensus mechanism is still present on private ledgers, it functions much differently than on a public blockchain network. Typically, the group required to reach consensus will depend on the conditions set for each specific type of transaction. This structure could require consensus across all parties, across a subset of parties, or just the ones involved in the transaction.
Given the sensitivity of data in the realm of financial services, a permissioned network is arguably far more appropriate for securitization. This network infrastructure facilitates a scenario in which each party is privy to only the specific data points relevant to them and nothing more – an essential requirement for any finance application.
The Securitization Lifecycle
With an appropriate ledger system in place, the securitization process can be further explored and a path forward determined. By examining each phase of the securitization process in detail, we can outline what it will take to push the industry forward and bring the entire securitization lifecycle on-chain.
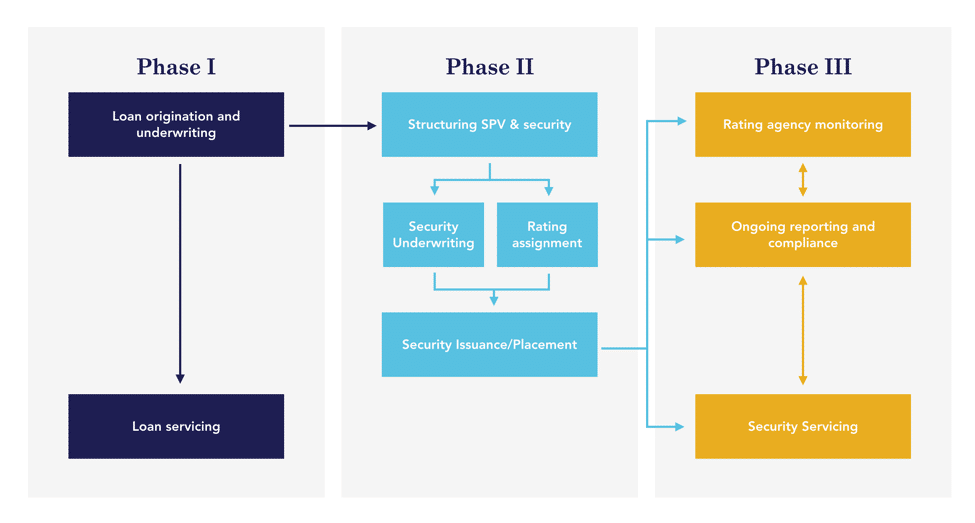
Phase I: Loan Origination and Servicing
Loan Origination
An originator begins by sourcing borrowers and underwriting individual loans. These loans are typically funded on-balance sheet via private term loans for younger originators and/or warehouse lines of credit from major banks for more mature originators. As the originator’s business grows, they typically have to source additional capital to help fund their ever-increasing loan book. This naturally leads to either having to secure more debt capital or selling loans.
Loan Servicing
Throughout the life of the loans, the originator or third-party servicer (depending on the arrangement) is responsible for servicing the assets. Servicing includes everything from collecting regular repayments to chasing down borrowers for payment. This process may also involve using recourse to collect funds in the event a loan becomes non-performing and the borrower defaults.
Phase II: Primary Issuance
Structuring SPVs and the Security
The originator works with an arranger (typically an investment bank) to sell their loans and bundle them together into bankruptcy-remote special purpose vehicles (SPVs). These SPVs become the economic owners of the loans and issuers of any securities. The arranger is also responsible for structuring the security, working with counsels on all legal aspects, appointing other relevant parties involved in the securitization process, and spearheading the marketing and distribution of the security.
Security Underwriting and Legal Review
One of the most time-consuming and resource-heavy aspects of securitization is the gathering of information, auditing of such information and legal sign-off on all elements of the transaction. Given the various stakeholders involved in the process, the underwriting and legal review process can take weeks to months depending on the complexity of the offering.
Rating Agency Assignment
Rating agencies are brought into the process once the structure has been formalized and legal review has been completed. The rating agency performs a thorough, objective analysis of the structure, the parties and the underlying assets and renders a rating for the benefit of providing investors a credible unbiased review of risks. They typically rely on audited information that both the company and the arranger provide for assessment.
Security Issuance / Placement
Finally, the offering is either underwritten and sold to investors via broker-dealer networks (public offering) or placed with investors via listing services (private offering). In either scenario, a risk transfer has occurred whereby the performance of the underlying assets is what dictates investors’ return in this security. On the flip side, the originator has monetized assets and has effectively sold their loan portfolio to security holders at an upfront discount commensurate with the various risks associated with the underlying loans and deal structure.
Phase III: Post Execution
Security Servicing
Once the security has been issued and begins to repay investors in the third phase of securitization, a pre-appointed trustee begins to manage the trust or SPV and all associated distributions. When repayments on underlying assets occur, the money is pooled into the SPV, sent to the trustee to proportionally allocate the distributions based on investors’ holdings, and is finally repaid to investors in the form of interest and principal.
Rating Monitoring
Once a rating has been rendered and the security has been issued, the rating agency will continue to monitor the health of all the various elements of the structure. Specifically, the bulk of this work pertains to gaining an accurate read of how the underlying pool of assets has performed since inception and since the last review. Should any trends of deterioration or improvement present themselves, the ratings are subject to change upon a more extensive re-evaluation.
Reporting and Compliance
As part of ongoing compliance with SEC regulations around periodic disclosures to investors and other stakeholders of the security, routine reporting is typically required. Such reports provide useful information and validation of both the security’s health and the health of the underlying assets. Compliance with regulators, lenders, auditors and other service providers is essential for a securitization to function and act in investors’ best interests.
Pursuing Securitization on a Distributed Ledger
In reviewing the multiple parties involved in the securitization process, it’s clear that distributed ledger technology offers a myriad of benefits and efficiencies. In the first phase of the securitization lifecycle, there is an opportunity to eliminate the need for extensive intermediary networks. Distributed ledger technology can bring originators and investors together in a peer to peer network. A blockchain network would also drastically reduce the time and effort required for servicing assets. Through the use of smart contracts, many of these activities can be automated.
In the second phase of the securitization lifecycle, blockchain could be used to issue securities in an efficient, immutable, and traceable environment. These digital assets would be the equivalent of “paper” securities but would be far easier to distribute and transfer without the involvement of financial intermediaries. Once again, smart contracts could be used to drastically reduce the legal paperwork required during this step in the process.
In the third phase of securitization, a smart contract could effectively take the place of a trustee. When repayments on underlying assets occur, this automated contract could be structured to complete the distribution process. Further, in utilizing digital assets, the process of buying and selling securities would be even more efficient with a broader reach. Rather than being restricted to a single country-specific exchange, these securities could be made available to a global investor pool. Reporting and compliance would also be streamlined as all of these third-parties would have access to the same underlying information they require.
As mentioned, several indicators suggest the future of asset securitization is on-chain. Permissioned ledgers can be used to build networks that effectively simplify the securitization process through automated processes and decentralized functionality. These efficiencies have the potential to streamline operations, lower costs, and improve transparency and security.

Nelson Chu is the founder and CEO of Cadence, the leading digital securitization and investment platform for private credit. He is a 3x startup founder with several years of experience at the top investment management firms, including Bank of America and BlackRock. Prior to Cadence, he founded a strategy consulting firm specializing in helping companies build products and raise capital for growth, creating over $1B in equity value. He currently serves as an advisor to an ultra high net worth family office and is an active angel investor, with notable investments including BlockFi, Cadre, Care/Of, Clover Health, dv01, Tala, and Uala.
Twitter: https://twitter.com/withcadence
Image by Gerd Altmann from Pixabay
More Articles:
Securrency Introduces CAT-20 and CAT-721, the World’s First Multi-Ledger Security Token Protocols
You Might also Like